Multi-factor authentication (MFA) is one of the most secure levels of cyber security businesses and individuals can use to keep their data safe online. With the increasing adoption of MFA, cybercriminals have shifted their tactics to exploit weaknesses in this otherwise robust security measure. One of the newest and most concerning techniques is the MFA fatigue attack, a form of social engineering designed to break through MFA defences by targeting the users themselves, overwhelming them with constant authentication prompts.
What is an MFA Fatigue Attack?
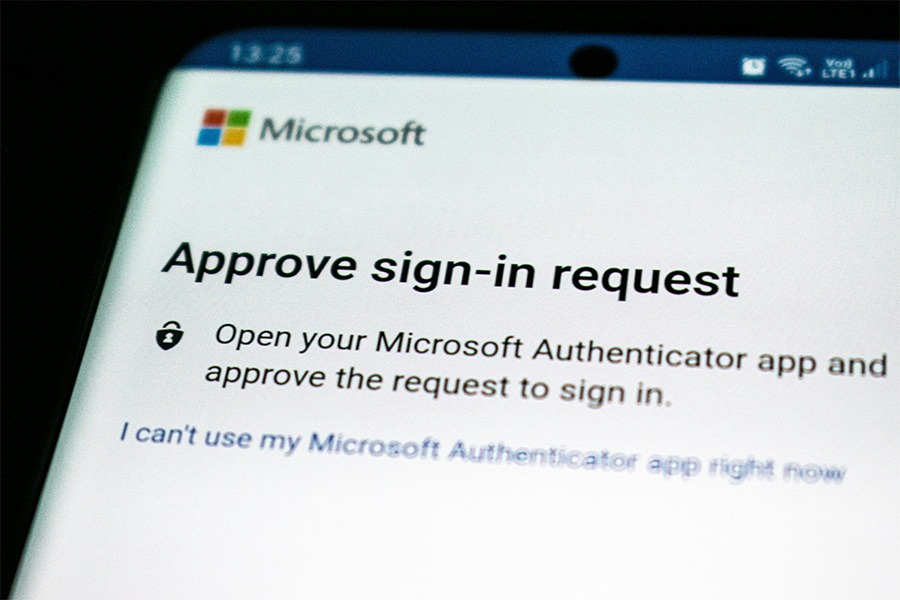
An MFA fatigue attack, also known as “prompt bombing” or “authentication fatigue,” is a cyberattack that targets users of multi-factor authentication systems. Its goal is to exploit human psychology rather than technical vulnerabilities, making it a dangerous social engineering tactic.
Here’s how it works:
- The attacker gains access to a user’s valid login credentials.
- When the attacker attempts to log in, the system sends an MFA request (e.g. a push notification or approval prompt) to the user’s device.
- The attacker keeps sending repeated MFA prompts, often at odd hours of the day or night, hoping the user will become frustrated or confused and eventually approve the request just to stop the bombardment.
The goal of the attack is to exploit fatigue or frustration in the user, causing them to mistakenly authorise the attacker’s login attempt.
Why Are MFA Fatigue Attacks Effective?
MFA fatigue attacks are effective because they exploit one of the weakest links in cyber security: humans. Even the most well-secured systems can be undermined if users fall victim to social engineering tactics.
How to Avoid MFA Fatigue Attacks
While MFA remains one of the most effective ways to secure accounts, it’s important to take additional steps to protect yourself and your organisation from MFA fatigue attacks.
Here are some best practices to prevent such attacks:
Use Number Matching or MFA with Context
One of the best ways to mitigate MFA fatigue attacks is to implement number-matching or context-based MFA. Instead of simply approving a generic push notification, the user is required to either match a number displayed on their device with one shown on the login screen or verify additional context, such as the location or device making the request.
Educate Users About MFA Fatigue Attacks
Organisations should train employees to recognise unusual or excessive MFA prompts as a potential attack. Reporting suspicious activity or changing passwords promptly after receiving a suspicious MFA request can prevent MFA attack fatigue by ensuring the hacker no longer has access to the correct login credentials.
By empowering users with knowledge, you reduce the likelihood of them falling for these tactics.
Implement Rate Limiting for MFA Requests
Configure MFA systems to limit the maximum number of authentication attempts allowed within a specific time frame. This prevents attackers from bombarding users with nonstop requests.
Enable Notifications for Suspicious Login Attempts
Many MFA providers allow users to receive alerts for unusual login attempts, such as logins from new devices, unexpected locations or outside of normal work hours. These alerts can help users and IT teams identify potential MFA fatigue attacks early.
Conclusion
MFA fatigue attacks are a stark reminder that even the most effective security measures can be undermined by social engineering. While MFA remains a critical tool for protecting accounts and we encourage the use of it for all businesses and personal users, organisations must take steps to guard against these emerging threats.
If you have any questions about your cyber security or are considering moving to cloud computing and want to ensure that you have the best MFA defences in place, get in touch with Inventas today. We have over 25 years of experience in IT infrastructure and are up-to-date with all the latest trends in cyber security.